BANGKOK, Apr 19, 2024 – (ACN Newswire) – In today’s interconnected world, digital technology permeates every aspect of our lives, transforming how we live, work, and interact. As Thailand advances its digital landscape, the importance of cybersecurity cannot be overstated. The Cyber Security Summit: Thailand aims to unite visionaries and industry leaders to address the challenges and opportunities in securing Thailand’s digital future.

Under the theme “Navigating Threats across Thailand’s Cyber Landscape,” the summit will focus on strategies, action plans, and best practices to develop and protect the nation’s cybersecurity sector and build a resilient digital ecosystem. Key topics of discussion will include transformative pathways for digital success, future-proofing data centers, unleashing the AI revolution, unlocking legacy systems, and navigating cyber resilience in the digital era.
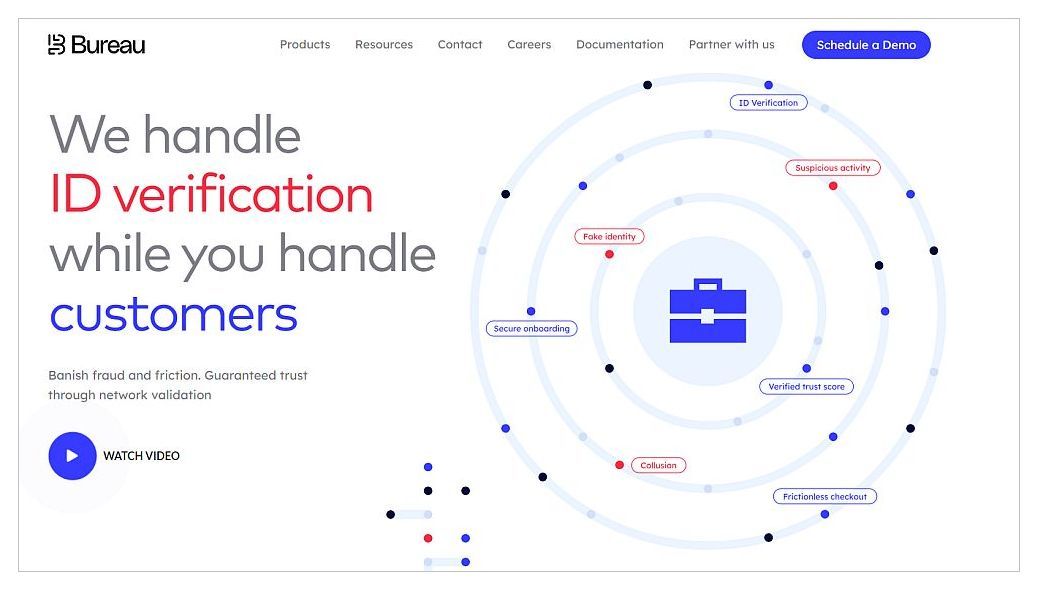
The Cyber Security Summit: Thailand, in its 22nd edition, continues to be a pivotal event in addressing cybersecurity challenges. Scheduled for 30th May in Sofitel Bangkok, it emphasizes Thailand’s growing importance in the digital domain. As an integral part of a prestigious global event series, this summit offers industry leaders a platform to explore strategies aimed at enhancing decision-making capabilities, driving operational efficiencies, and nurturing a pervasive digital ethos. It underscores the urgency of proactive cybersecurity measures and Thailand’s role in navigating the dynamic cyber landscape.
key highlights of the 22nd Edition Cyber Security Summit, Thailand
1. Esteemed Speaker Lineup: Featuring top cybersecurity experts and industry leaders.
2. Theme: “Navigating Threats across Thailand’s Cyber Landscape”: Addressing proactive approaches to enhance critical infrastructure capabilities and raise cybersecurity awareness.
3. Actionable Insights: Attendees will gain practical strategies and best practices to develop and protect the nation’s cybersecurity sector.
4. Networking Opportunities: Facilitating collaboration and knowledge exchange among cybersecurity professionals.
Esteemed Speaker Lineup: Featuring prominent cybersecurity experts and industry leaders such as:
- Jadet Khuhakongkit, Assistant Secretary General, National Cyber Security Agency, Kingdom of Thailand
- Athikom Kanchanavibhu, Chief Information Security Officer: Executive Vice President, Digital & Technology Transformation, Mitr Phol Group
- Yaron Slutzky, Chief Information Security Officer, Agoda
- Phong Sam, Chief Information Security Officer, Central Group
- George Papas, Chief Information Security Officer, Asian Tigers Group Thailand
- Daniel Lui, Chief Information Officer, Pacific Healthcare Group
- Chatchawarn Jirupathum, Group Information Security and Data Protection Officer, RMA Group Co. Ltd.
- Narudom Roongsiriwong, Senior Vice President – Global Enterprise Architecture and Cyber Security, Banpu Public Company Limited
About the cyber security summit Thailand
The Cyber Security Summit (CSS) Thailand is a premier event that convenes cybersecurity leaders from various sectors in Thailand. It provides a platform for sharing insights, strategies, and best practices to enhance cybersecurity resilience and awareness in the country. With esteemed speakers, interactive discussions, and networking opportunities, CSS Thailand fosters collaboration and promotes a proactive approach to cybersecurity, ultimately contributing to Thailand’s cybersecurity readiness and resilience.
For more information on the Cyber Security Summit Thailand, visit: https://exito-e.com/cybersecuritysummit/thailand/
About Exito
Exito, which means success in Spanish, embodies our commitment to the success of our customers. Each year, we host over 240 virtual and in-person conferences globally, bringing together audiences with world-class thought leaders and C-level executives across industries. Our meticulously crafted agendas, based on extensive research and valuable industry insights, facilitate business, knowledge transfer, deal flow, and impactful messaging for brands.
For Media Enquiries, contact:
Kasturi Nayak (Sr. Marketing Executive)
Kasturi.nayak@exito-e.com
Enquiry@exito-e.com
Exito Media Concepts
Copyright 2024 ACN Newswire. All rights reserved. http://www.acnnewswire.com